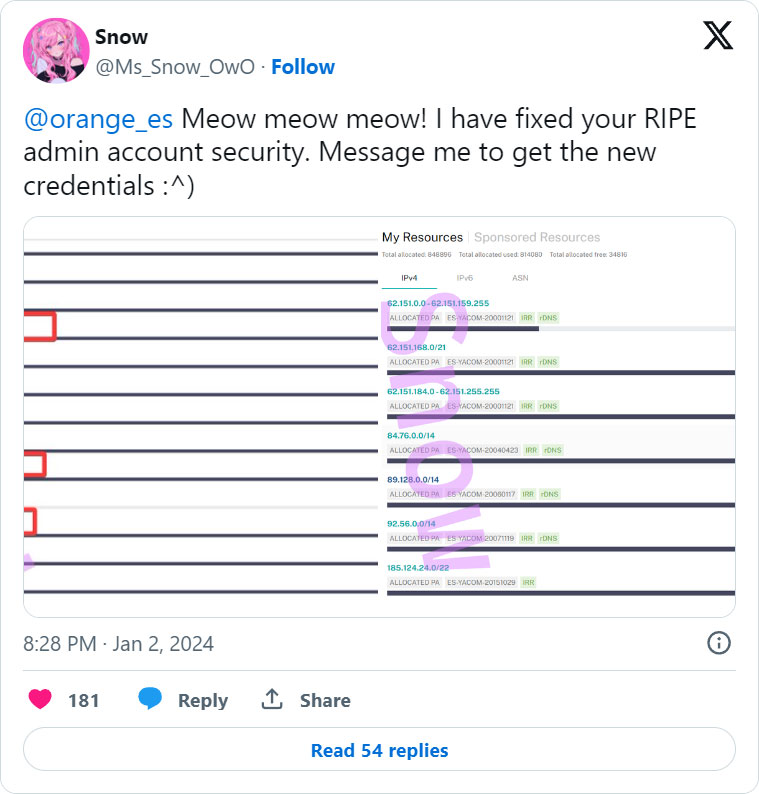
Orange Spain suffered an web outage at the moment after a hacker breached the corporate’s RIPE account to misconfigure BGP routing and an RPKI configuration.
The routing of visitors on the web is dealt with by Border Gateway Protocol (BGP), which permits organizations to affiliate their IP addresses with autonomous system (AS) numbers and promote them to different routers they’re linked to, often called their friends.
These BGP ads create a routing desk that propagates to all different edge routers on the web, permitting networks to know one of the best path to ship visitors to a selected IP tackle.
Nonetheless, when a rogue community proclaims IP ranges often related to one other AS quantity, it’s potential to hijack these IP ranges to redirect visitors to malicious web sites or networks.
In line with Cloudflare, that is potential as a result of BGP is constructed on belief and the routing desk might be up to date primarily based on which advertiser has the shortest and extra particular route.
To forestall this, a brand new customary known as Useful resource Public Key Infrastructure (RPKI) was created that acts as a cryptographic answer to BGP hijacking.
“Useful resource Public Key Infrastructure (RPKI) is a cryptographic methodology of signing data that affiliate a BGP route announcement with the right originating AS quantity,” explains a Cloudflare article on RPKI.
By enabling RPKI with a routing physique equivalent to ARIN or RIPE, a community can cryptographically certify that solely routers beneath their management can promote an AS quantity and their related IP addresses.
Hacker breaches RIPE account to interrupt BGP
Yesterday, a risk actor named ‘Snow’ breached the RIPE account of Orange Spain and tweeted to Orange Spain to contact them about getting new credentials.
Since then, the attacker modified the AS quantity related to the corporate’s IP addresses, and enabled an invalid RPKI configuration on them.
Saying the IP addresses on another person’s AS quantity after which enabling RPKI successfully precipitated these IP addresses to not be introduced correctly on the web.
“As we see, what they did was create some ROA /12 data, which mainly point out who’s the AUTHORITY over a prefix (i.e., the AS that may announce it),” Felipe Cañizares, CTO from DMNTR Community Options, advised BleepingComputer.
“These grouped collectively the /22 and /24 prefixes introduced by Orange Spain, indicating that the AS that ought to announce that prefix was AS49581 (Ferdinand Zink buying and selling as Tube-Internet hosting).”
“As soon as this was achieved, they activated RPKI on that /12… and goodbye…”
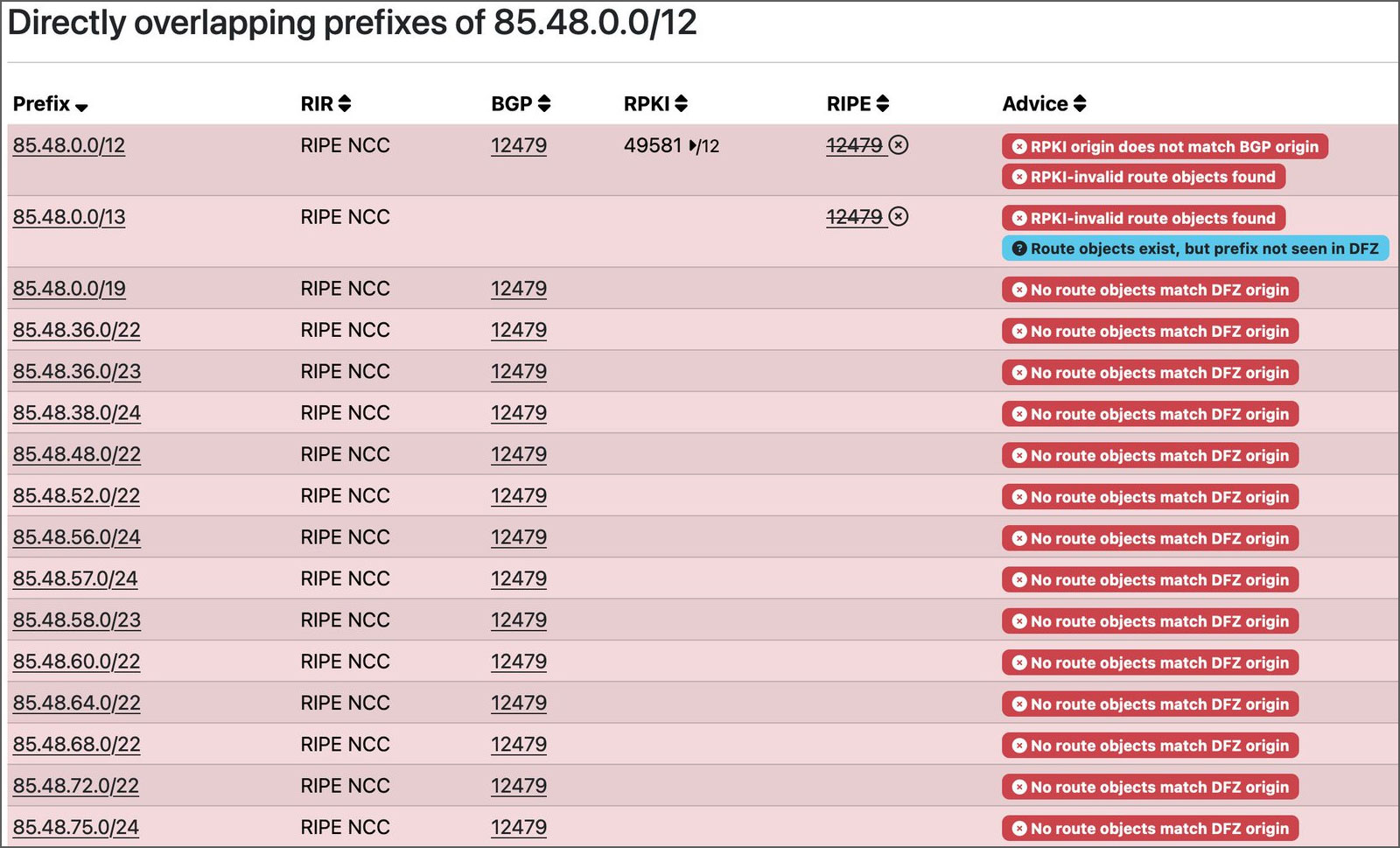
Supply: Cañizares
This led to a efficiency subject on Orange Spain’s community between 14:45 and 16:15 UTC, which might be seen within the Cloudflare visitors graph under for AS12479.
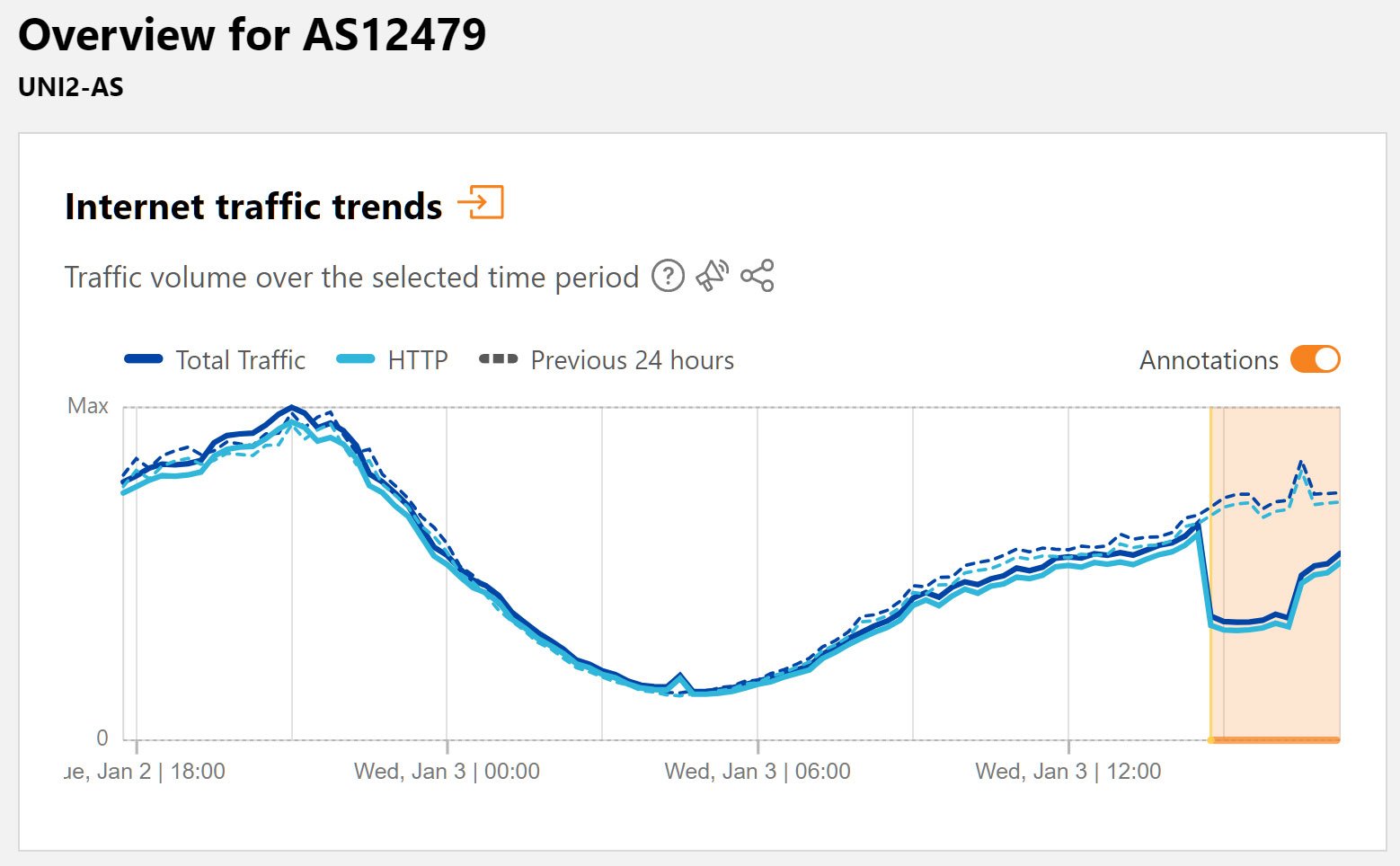
Supply: Cloudflare
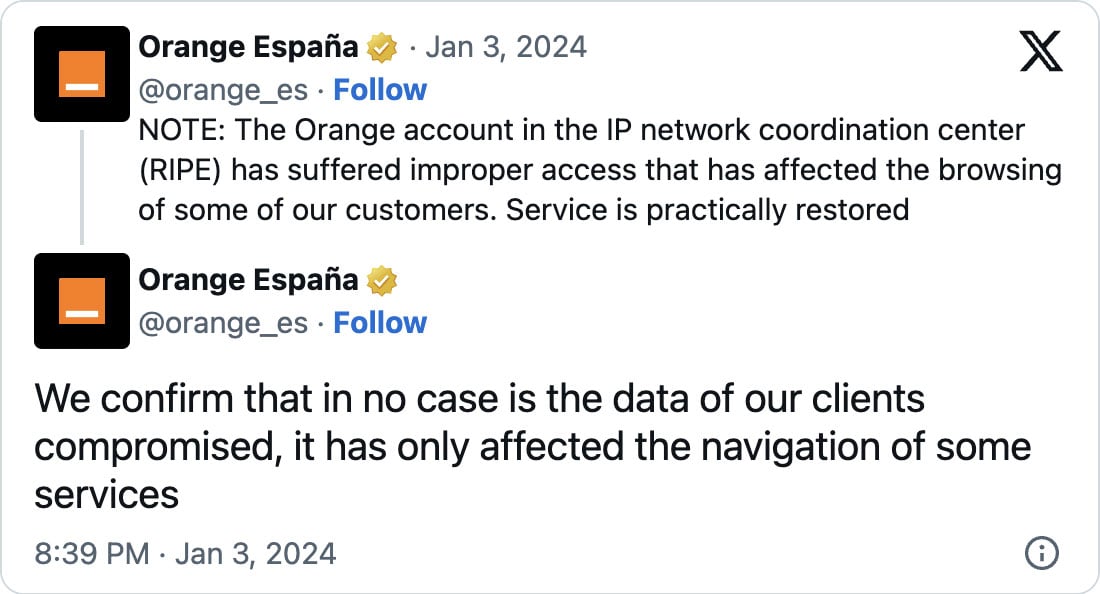
Orange Spain has since confirmed that their RIPE account was hacked and has begun to revive providers.
“NOTE: The Orange account within the IP community coordination heart (RIPE) has suffered improper entry that has affected the searching of a few of our clients. Service is virtually restored,” Orange Spain tweeted.
“We affirm that in no case is the information of our purchasers compromised, it has solely affected the navigation of some providers.”
It’s unclear how the risk actor breached the RIPE account however Cañizares advised BleepingComputer that he believes Orange Spain didn’t allow two-factor authentication on the account.
Cañizares has created a thread on X summarizing how this assault occurred.
BleepingComputer contacted Orange Spain with questions concerning the assault however has not acquired a reply right now.
Credentials probably stolen by way of malware
Whereas Orange Spain has not disclosed how its RIPE account was breached, the risk actor supplied a clue in a screenshot posted to Twitter that contained the hacked account’s e mail tackle.
Alon Gal of cybersecurity intelligence service Hudson Rock advised BleepingComputer that this e mail and an related password for the RIPE account have been present in an inventory of accounts stolen by information-stealing malware.
“The Orange worker had their pc contaminated by a Raccoon sort Infostealer on September 4th 2023, and among the many company credentials recognized on the machine, the worker had particular credentials to “https://entry.ripe.internet” utilizing the e-mail tackle which was revealed by the risk actor (adminripe-ipnt@orange.es),” explains analysis from Hudson Rock.
In line with Gal, the password for the account was ‘ripeadmin,’ which is a very simple password for a important account.
Data-stealing malware has change into the bane of the enterprise, as risk actors use them to collect credentials for preliminary entry to company networks.
Menace actors generally buy stolen credentials from cybercrime marketplaces, that are then used to breach networks to carry out knowledge theft, cyber espionage, and ransomware assaults.
For that reason, all accounts should have two-factor or multi-factor authentication enabled in order that even when an account is stolen, attackers can’t log in to the account.